A recently disclosed F5 BIG-IP vulnerability has been used in destructive attacks, attempting to erase a device’s file system and make the server unusable.
Last week, F5 disclosed a vulnerability tracked as CVE-2022-1388 that allows remote attackers to execute commands on BIG-IP network devices as ‘root’ without authentication. Due to the critical nature of the bug, F5 urged admins to apply updates as soon as possible.
A few days later, researchers began publicly publishing exploits on Twitter and GitHub, with threat actors soon using them in attacks across the Internet.
While most attacks have been used to drop webshells for initial access to networks, steal SSH keys, and enumerate system information, SANS Internet Storm Center saw two attacks that targeted BIG-IP devices in a much more nefarious manner.
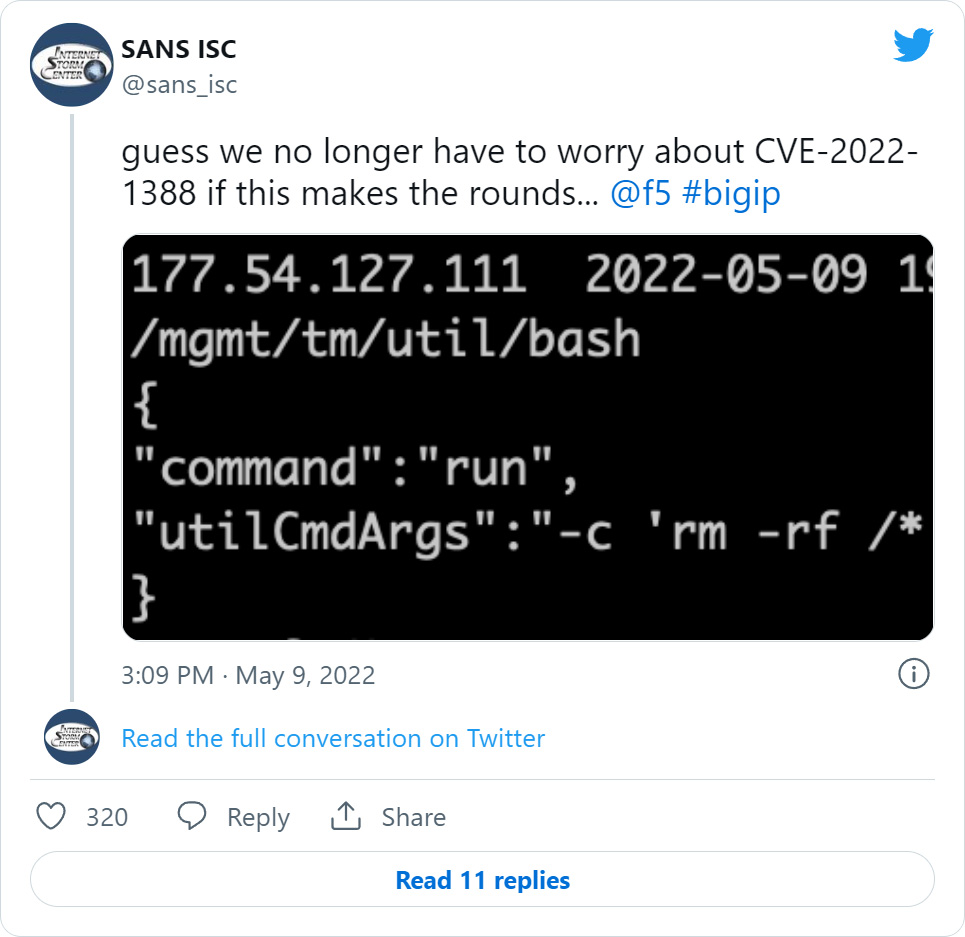
SANS told BleepingComputer that their honeypots saw two attacks coming from IP address 177.54.127[.]111 that executes the ‘rm -rf /*’ command on the targeted BIG-IP device.
This command will attempt to erase all of the files on the BIG-IP devices’ Linux file system when executed.
As the exploit gives attackers root privileges in the Linux operating systems powering BIG-IP devices, the rm -rf /* command will be able to delete almost every file, including configuration files required for the device to operate correctly.
After publishing our story, security researcher Kevin Beaumont confirmed that devices were being erased this evening.
“Can confirm. Real world devices are being erased this evening, lots on Shodan have stopped responding,” tweeted Beaumont.
Thankfully, these destructive attacks do not appear to be widespread, with most threat actors looking to benefit from breaching the devices rather than causing damage.
Cybersecurity threat intelligence firms Bad Packets and GreyNoise told BleepingComputer that they had not seen any destructive attacks on their honeypots.
greynoise researcher kimber said they mostly see the exploits drop webshells, exfiltrate configs, or run commands to create admin accounts on the devices.
While the destructive attacks seen by SANS may be rare, the fact that they are happening should be all the incentive an admin needs to get their devices updated to the latest patch levels.
When we contacted F5 about these destructive attacks, they told BleepingComputer they are in contact with SANS and strongly advise admins not to expose the BIG-IP management interface to the Internet.
“We have been in contact with SANS and are investigating the issue. If customers have not already done so, we urge them to update to a fixed version of BIG-IP or implement one of the mitigations detailed in the security advisory. We strongly advise customers never to expose their BIG-IP management interface (TMUI) to the public internet and to ensure the appropriate controls are in place to limit access.” – F5
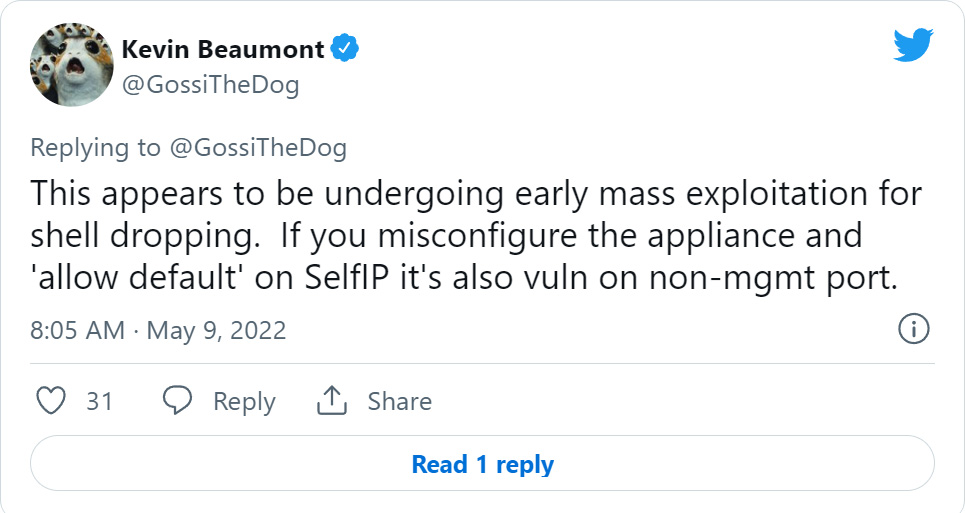
However, it is important to note that Beaumont found that attacks are also affecting devices on non-management ports if they are misconfigured.
For those affected by attacks on their BIG-IP devices, F5 told BleepingComputer that their Security Incident Response Team is available 24 hours a day, seven days a week, and can be contacted at (888) 882-7535, (800) 11- 275-435, or online.
For F5 BIG-IP admins concerned their devices were already compromised, Sandfly Security founder Craig Rowland is offering test licenses that they can use to check their devices.
Update 5/10/22: Added confirmation from Kevin Beaumont.